Category: Software Development
In the rapidly evolving world of software development, security can be viewed as a critical element of the development process rather than an afterthought. Software development is now of immense importance for almost every business, and security has become a prerequisite for all of us. This is where DevSecOps comes in.
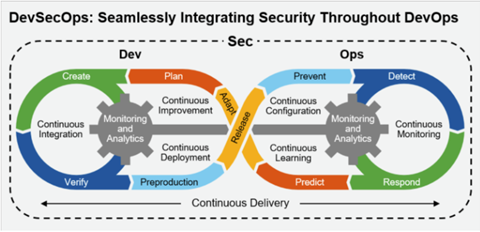
It is a proactive approach to software development that combines development (Dev), security (Sec), and operations (Ops) into one integrated process. DevSecOps helps developers adopt a security-first mindset and integrate security into the software development process.
This blog can be your gateway to understanding the power and potential of DevSecOps. We will explore how it transforms the way we build, deploy, and protect software, making security an integral part of the development process from the very beginning.
Understanding DevSecOps
DevSecOps is a natural progression from the earlier concept of DevOps, which focused on breaking down the silos between development and operations teams to improve collaboration, efficiency, and the speed of delivering software.
DevSecOps builds on these principles by bringing security to the forefront of software development. Rather than treating security as a separate phase that comes after development, it recommends “shifting left”, meaning security is prioritized from the earliest stages of the software development lifecycle.
Why DevSecOps Matters
DevSecOps is essential for several reasons:
- Proactive Security
With cyber threats becoming increasingly sophisticated and prevalent, addressing security from the outset becomes crucial. DevSecOps allows organizations to proactively identify and mitigate vulnerabilities during development, reducing the risk of security breaches.
- Faster Development
Contrary to the misconception that security hinders the pace of development, integrating security practices streamlines the process. By identifying and fixing security issues early, teams can avoid costly delays and rework in later stages.
- Compliance
Many industries have strict regulatory requirements for data protection and security. DevSecOps helps organizations ensure that they meet compliance standards without adding extra overhead.
- Collaboration
DevSecOps promotes a culture of collaboration. It breaks down the barriers between development, security, and operations teams, fostering open communication and knowledge sharing.
- Continuous Improvement
DevSecOps emphasizes automation, continuous monitoring, and feedback loops. It means that as your software evolves, you can continuously improve your security practices.
DevSecOps Principles
Implementing DevSecOps involves adhering to several core principles:
- Shift Left: Address security early during the development process, from design and coding to testing.
- Automation: Automate security checks and testing as much as possible to ensure consistency and efficiency.
- Collaboration: Create a culture of shared responsibility for security. Continual collaboration and knowledge sharing must be encouraged between teams.
- Continuous Monitoring: Continuously monitor applications and infrastructure to detect and respond to security threats in real time.
- Security as Code: Write security configurations and policies as code, enabling easy integration into the development process.
DevSecOps Best Practices
- Automate Security Testing
Use automated tools for code scanning, vulnerability assessments, and compliance checks. These tools can identify issues early in the development process.
- Secure Coding Training
Provide training to developers on secure coding practices. Knowledgeable developers are less likely to introduce vulnerabilities in the first place.
- Continuous Monitoring
Implement continuous monitoring of your applications in production. It allows for the early detection of potential security threats.
- Shift Left
“Shift left” security by bringing it closer to the development phase. It involves integrating security testing into the initial stages of development.
- Use Containers and Microservices
These technologies enable easy security management in a dynamic environment, making it effortless to isolate, update, and secure components of your applications.
- Regularly Update Dependencies
Keep your software dependencies up to date to patch vulnerabilities as and when they are discovered.
DevSecOps Challenges
Although DevSecOps provides numerous benefits, it presents a few challenges and risks:
- Cultural Resistance
Changing the organization’s culture can be difficult, especially when it involves breaking down silos and redefining roles and responsibilities.
- Tool Integration
Selecting and integrating the right security tools can be complex, and we must ensure they work seamlessly with the development process.
- Resource Constraints
Implementing DevSecOps requires investment in tools, training, and personnel. Smaller organizations may find it challenging to allocate these resources.
- Skillset
Development, operations, and security expertise are crucial for DevSecOps. If not planned well, evaluating the talents of your team, providing them with new roles, and upskilling them can be a complex process.
In conclusion, DevSecOps is not just a methodology; it is a fundamental shift in how we perceive software development. By placing security at the core of the development process, organizations can build robust, resilient, and secure applications that are well-equipped to face the ever-evolving challenges of the digital age.
The synergy between Development, Security, and Operations is not just a trend; it is a necessity in today’s threat landscape. DevSecOps ensures that security is not a roadblock but an enabler, allowing businesses to innovate, grow, and thrive while safeguarding their digital assets.
By embracing DevSecOps, you are not just building software; you are building trust, confidence, and a brighter future for your organization and your valued customers.
To know more about our DevSecOps best practices, services and approaches please visit our website or book a free consultation with our expert DevOps Team today!
References:
DevSecOps Best Practices to Implement. (TechRepublic)
In recent times, there has been a great evolution in the field of software testing. New technologies have brought in the latest updates in the software development lifecycle.
Independent Software Vendors (ISVs) of all sizes have been adapting to the continuous changes and demands of the customers. There is always competition in delivering a superior product to stay relevant to the market.
Software testing is an important phase of the development lifecycle. End-to-end testing is the key driver that helps organizations build customer loyalty, and brand visibility, and boost profits.
Top challenges faced by ISVs in software testing
- Flexibility in keeping up with the business’s changing requirements.
- Rush to release products to market to keep up with the competition.
- Poor product quality due to an unsupported testing process.
- ISVs especially start-ups need to redefine their product strategy.
- Finding ways to recruit and retain talent.
Adoption of a continuous software testing process in line with the competitive demands helps deliver high-quality applications and products.
Benefits of software testing
- Improved time to market: by testing software during the early phase of the development lifecycle, the quality of the development improves.
- Improved quality through more automated tests: The quality of the application software is improved by performing continuous tests and verifying each component during the development phase.
- Continuous testing: due to continuous testing during every phase of the software development life cycle (SDLC), the risks are lowered as they are recognized and addressed earlier in the process ensuring the quality of work.
Major trends in software testing, a few are discussed below:
User Acceptance Testing (UAT) – UAT is an important test that is performed in the final phase, to test whether the software is functioning as per the requirements.
Regression Testing – this is an effective test that must be implemented especially when there is a continuous change in the customer requirements that are dictated to ISVs.
Automation Testing –test automation helps speed up the testing process and ensures faster time to market.
Performance Testing –high-performing digital mobile and web apps, that experience varying loads, are bound to deliver a great customer experience.
Selenium Testing – this is the common test automation tool used for faster releases that author functional tests without the necessity for the tester to have the knowledge of the test scripting language. This tool majorly helps in optimizing the testing costs, generating quicker ROI.
Would you like to know more about our experience in software testing? Contact us and we will get back to you quickly.
“If you can’t build a well-structured monolith, what makes you think microservices is the answer?” Simon Brown
“Monolith to microservices” is become quite a familiar phrase range from more than 70% of technology leaders today. Nowadays, It appears like everyone is into microservices, and monolith architectures are slowly fading into obscurity. Organizations implement a microservices strategy for designing and detailing an application as a group of loosely coupled services that interact among themselves to deliver a stated business objective.
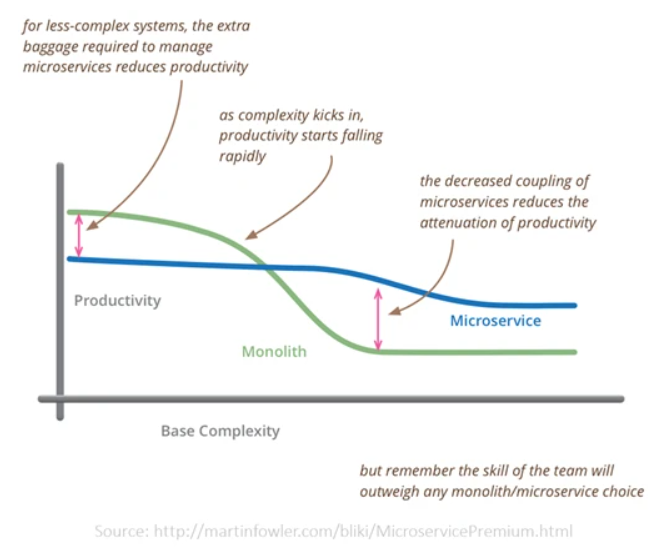
The Microservices Architecture is a variant of the Service-Oriented Architecture (SOA)—an evolved development approach that has emerged from the world of domain-driven design. Each microservice has a specific function. Yet together they form a complete application, or they perform a global task. Developers can deploy and test each microservice independently. Modern IT workflow consider Microservices as the first step to embrace a DevOps culture that—:
- Enables efficient computing
- Aids in building resilient applications
- Increased business process agility,
- Improved scalability and manage multiple things at a time
- Faster delivery and deployment to market
An “S” pattern adoption curve validates that there are numerous use cases in which companies benefit from using microservices to develop and deploy applications.
Originally, the technology begins as a great idea due to a need in some pockets, and the solution is developed to satisfy that need. People start considering it as an interesting technology for the future. Then, as its popularity spreads, the technology keeps upgrading on the coolness factor, and the recognition goes beyond the niche use-cases. You may get a clear idea of the concept from the below “coolness factor.”
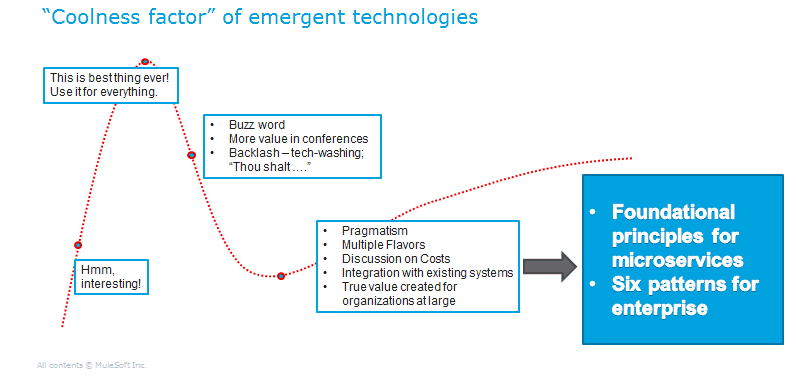
Conceptually, Microservices prolong the same principles that engineers have exercised for decades. Microservices implementation poses its challenges like most transformational trends. Organizations also notice increased complexity and effort to develop applications with a microservice framework by examining several use cases. In this article, we will discuss some challenges associated with building and deploying microservices including when you should not use microservices. Let’s have a look.
Challenges of Microservices
a. Design
Organizations face increased complexity when designing microservices compared to monolithic apps. Microservice Architecture is about splitting large, complex systems vertically (based on functional and business requirements) into smaller subsystems that are independently deployable. These sub-systems communicate with each other via a lightweight, language-agnostic network is known as either synchronous (e.g. REST, gRPC) or asynchronous way. If you are using Microservices first, you may face few difficulties such as:
- Confusions regarding each microservice’s size and a higher number of Moving parts (Services, Databases, Processes, Containers, Frameworks).
- Optimal boundaries and connection points between each microservice
- Designing the entire framework to integrate services is harder and time-consuming.
There are multiple design patterns in microservices architecture, but I will discuss Database per Microservice to make the idea crystal clear. If you are interested to know more about the other design patterns, check out Microservices architecture.
The database is the most important decision company faces once it replaces the large monolithic system with many smaller microservices. Many architects prefer having the database as it is, even when they migrate to microservice architecture. It is an anti-pattern, especially in a large-scale system, while it provides some short-term advantage, as the microservices will be tightly coupled in the database layer. A better approach is to provide every Microservice its Datastore, so that there is no strong coupling between services in the database layer. The bespoke design approach will also ensure that the Microservices are correctly segregated according to the Domain-Driven-Design.
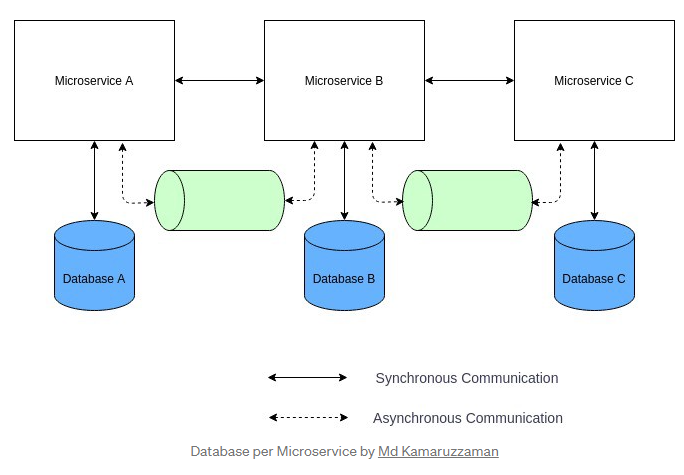
But here you may face difficulties Sharing data among services and Giving application-wide ACID transactional guarantee becomes a lot harder. Decomposing the Monolith database to smaller parts needs careful design which is another challenging task. Hence it is recommended to use this design approach while you are working in small-scale applications and one single team can develop all the Microservices.
A bounded context is required for designing microservices requires. Accordingly, every microservice should illuminate, encapsulate, and define a specific responsibility. To apply the same techniques for each responsibility/function, developers usually use a data-centric view when modeling a domain. This is the most challenging approach as, without logic, the data is pointless.
b. Security
Often Microservices are deployed across multi-cloud environments, that results in high-risk factor and loss of control on the visibility of application components—developers considering these additional vulnerable points. Unfortunately, security testing has not evolved quickly enough to address the risks introduced by this mass adoption of microservices. Vulnerabilities will appear in production if these concerns are not addressed in the SDLC. In addition to this challenge, each microservice communicates with others via various infrastructure layers, which makes testing even harder for these vulnerabilities.
Data security is another paramount concern within the microservices-based framework. Within such a framework data remains distributed. Confidentiality and integrity are correlated. Organization adapts this kind of tricky exercise to maintain the confidentiality, integrity, and privacy of user data.
The monolith application is manageable as you have one single thing to secure. Monolithic architectures are arranged in a single block (sic) and data is usually stored in one storage system. If we break down pillars, well, we can see that the monolith has to handle each pillar.
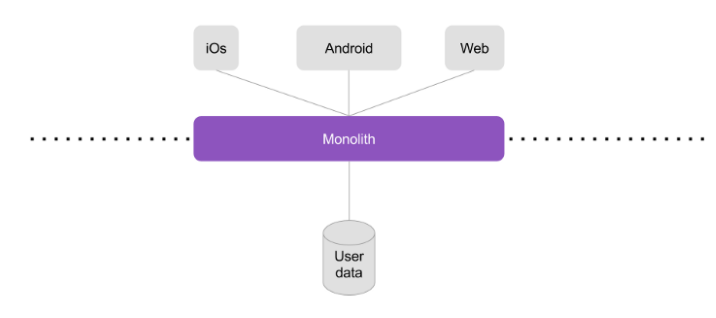

Now, if we are with a distributed architecture, Where we can consider 3 layers: clients (android, ios, web, …), API Gateways (or Backend for Frontend, BFF), and microservices and their data. There is responsibility segregation through the different layers. Mechanically, microservices are handling integrity, meanwhile exposed layers and front layers are taking care of confidentiality. Accessibility is also shared among all the panels as if they are not accessible, the platform is not functioning.


With microservices, the attack surface increases manifold. You need to take care of all the weaknesses they might expose for each one. Simple security-related bugs or plain old vulnerabilities in supporting libraries or their runtime environment can be the flaws in their design. As a result of this distributed framework, setting up access controls and administering secured authentication to individual services poses a technical challenge as well as increases the attack surface substantially.
c. Testing
The phase of testing is much more complex in microservices-based architecture than any software development lifecycle (SDLC). You must test individual services independently following the standalone nature of each microservice.
When we implemented multiple microservices in larger projects, the focus of the teams must have been on their microservices, resulting in a frequent lack of integration and testing approach. For instance, logging would be performed in a distinct format for complex microservices.
However, The different format was making it difficult to get all the essential information out of the log. Development teams also have to factor in integrating services and their interdependencies in test plans to manage these kinds of complexities.
d. Increased operational complexity:
Once a microservice is built, it needs to be deployed in several testing environments, and later in the production environment. As each microservice team is empowered to decide on its own, which technology to use, how to deploy the service, and where or how to run it, each microservice will most likely be deployed and operated in a different way.
- Traditional forms of monitoring are not sufficient for a microservices-based application. Suppose a request from the user interface traverses multiple services before getting to the one that can fulfill its request. The outcome of this traversal is a convoluted path of services, and without the proper monitoring instruments, recognizing the underlying cause of an issue is not only tricky—it’s often impossible.
- Scalability — an operational challenge associated with microservices architecture. Successfully scaling your microservice-based applications is challenging, although the scalability of microservices is often touted as an advantage. At the heart of these challenges lies something of a paradox.
To clarify the challenge, here I’m giving an example of two scenarios. When you are operating a single monolithic application from a single server, you can control an increase in demand by allotting more resources to the application. Or else, the individual user making use of an application, running new instances of it, and spread the load evenly in response to high demand.
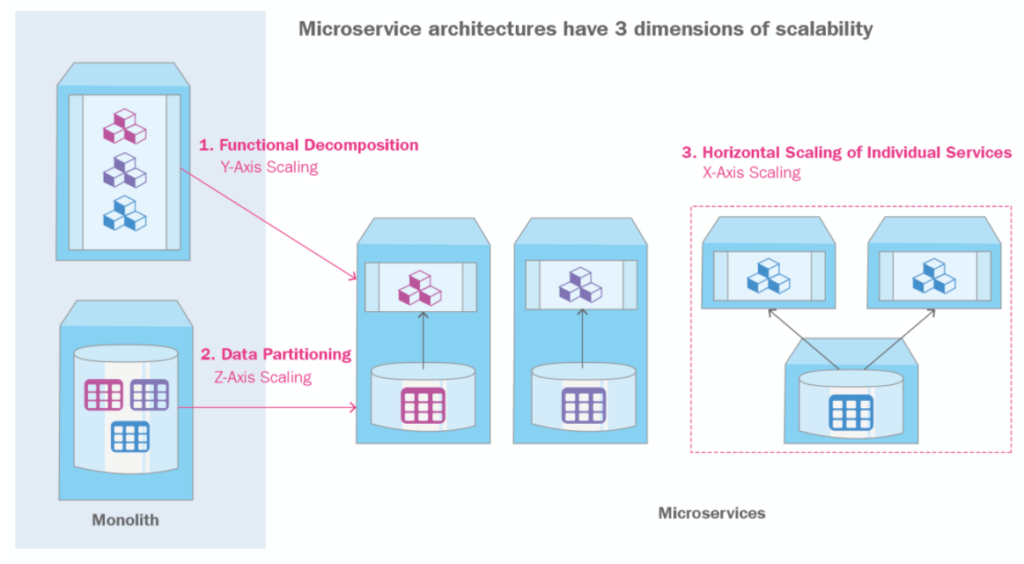
With microservices, on the other hand, upscaling can involve handling several different components and services. This indicates either all the elements need to upscale at the same time, or you need a means of identifying which individual components to upscale, as well as a method of assuring that they can still integrate with the rest of the system.
- Optimizing and scaling require more complex coordination. In a typical microservices framework, an application is broken down into smaller-independent services, hosted, and deployed across separate servers. Another challenge in this architecture is coordinating individual components, particularly when you experience a sudden spike in application usage.
- Fault tolerance is needed for every service. Enterprises demand their microservices to be resilient enough to confront internal and external failures. In a microservices-based application, one component failure can affect the entire system. Therefore, the framework you use must follow a design that considers error tolerance for each service that prevents the entire application from failing in the case of individual service downtime.
e. Complexity in communication:
Microservices that are deployed independently act as miniature standalone applications that communicate with each other. Hence, you have to configure infrastructure layers that enable resource sharing across services.
A poor configuration may lead to:
- Increased latency
- Reduced speed of calls across different services.
In this condition, you’ve received a non-optimized application with a slow response time. All the dependencies that used to be hidden in the monolith, coded in dependency rules between components, now have to be coded in the infrastructure configuration. However, Infrastructure communication is more tricky to maintain, no (not yet) development environment gives you red error indicators when IP addresses or ports mismatch between producer and consumer.
When to avoid Micro services:
Every enterprise moving to a new framework should perform thorough due diligence to ensure it’s the right fit.
These three situations will always help you explore microservices, decide when to skip the architecture for your chosen application.
When your defined domain is unclear or uncertain
Microservices have always been created within a bounded context. Now, think! Sometimes it ecomes logically tricky to break down your business requirements into specific domains as well as it will be equally difficult for you to create adequately sized microservices.
Another challenge of designing a proper means of communication among different services—this complexity is likely too much for you to realize maximum benefits in microservices. Here is the explanation of how an undefined or unclear domain causes difficulties for an organization.
Now, IT organizations embrace a system paradigm across all non-trivial business domains, event-oriented collaboration patterns have become a mainstay of such microsystem architecture design. These pitfalls tend to become a big bottleneck that thwarts event-oriented thinking on the journey toward evolutionary system design. To avoid these pitfalls, IT organizations must ensure that no microservice is designed without an explicit alignment and traceability with the business capability of the domain, as advocated by the bounded context strategy of domain-driven design.
Let’s explain a scenario. Sometimes, clients from the consumer lending domain desire to enable innovation and improve speed-to-market by transforming a single monolithic application into microservices with little or no focus on the design aspect of microservices. The circumstances can cause 500-plus microservices with extreme complexity leading to performance bottlenecks due to chatty inter-service communication.
Considering this kind of challenge, IT specialists always recommended a domain-driven rationalization to address this situation. This not only helps address performance challenges but also ensures the evolution of the application completely autonomously.
Hence, in the coming years, you need to be wiser about your domain design, and if you are not sure it’s wise not to use a micro services-oriented approach.
When improved efficiency isn’t guaranteed
No organization would not prefer to add up complexities and effort to adopt a culture without gaining improved efficiency. The idea of adopting Microservices is to embrace a DevOps culture that in turn:
- Employs automation: Microservices enhance agility, which fuels the ability to roll out new service versions. That agility is helpful for shorter build, test, and deploy cycles. Microservices can also
- Reduces cost and effort: A fault with a microservice only affects that microservice and its consumers. When monolithic applications experience an error, the entire monolith may break. Hence you may handle maximum work with minimum effort.
- Brings operational efficiency: it also incorporates the flexibility needed to employ service-specific security, replication, persistence, and monitoring configurations.
- Scalability: Organisations can scale up microservices independently by using pools, clusters, grids. That deployment feature makes microservices an excellent match for the elasticity of the cloud.
- Easy to manage: Microservices can leverage the agile methodology, where the application development effort is divided across teams that are smaller and work more independently.
Team strength is another major consideration for applying microservices architecture. For example, consider a relatively small development and operations team maintains the moderately large, moderately complex application. If it’s monolithic, the interactions between individual services may be very direct and may be optimized for specific tasks as required. A small development team is familiar with the code, and maintenance relatively simple for them.
If the same team needs to manage a microservice-based version of the same application, however, their overhead in terms of time and effort may increase significantly. Sometimes the architecture requires more coding time to implement even a minor change in data being handed from one service to another—and small design changes may require changes to the microservice orchestration and management system. It may create strain on the resources of the operations team, as well as the developers.
Hence, first, carry out your due diligence to verify if transitioning to a microservices framework helps achieve these goals.
When your application size is small or uncomplex
When your application size does not justify the need to split it into many smaller components, using a microservices framework may not be ideal. If your applications are already small enough, then there’s no need to break it further.
Remember that the idea of using a microservices framework is to break a complex application into a bunch of different, smaller services. When an application code is not complicated —already small enough and straightforward—transitioning it to a microservice framework will add complexities.
How could you measure Microservices as are the best choice for you?
If the benefits of using microservices outweigh the cons, then of course it is the best choice for you. But you should compare the business benefit with the effort and money you spent to set up the whole infrastructure and apply the approach.
While adopting a Microservice Architecture offers faster delivery and improved efficiency, businesses should deliberate carefully whether to opt for this approach. The benefits of transitioning from a monolithic to the microservices model are a dime a dozen—but there are still challenges to consider.
Here is one of our experiences! We have used Microservices architecture for a FinTech Application system because of its value regarding agility, scalability, and availability. The solution makes clients’ operation five times easy and gets a great response from the end-user level. Hence, for better guidance, you can always reach out to us.
2020 has proven this decade will be dramatically different than the one before it with so much change and volatility. The Covid-19 pandemic has allowed many businesses an opportunity to reboot their way of thinking and reinvent their approach in the field of modern software development. Software services companies are now leading other industries to inculcate the way of modern software development.
Cloud-centric software companies now can change, tune, tweak, and augment the functionality of the different parts of the software if they want. “Modern software development is about acknowledging the landscape of libraries and tools and applying them. The knowledge of creating an optimal algorithm is no longer required. Modern software development platforms become agile and move on from the traditional coding process of the 90s that required a sophisticated application” as mentioned by our CEO Apratim Ghosh.
Now the hidden question is how modern software development trends will be reshaping the organization’s future and how software developers are going to accommodate this in 2020 and beyond?
1. AI-powered business process
The growth of AI-powered businesses will exponentially increase in the next few years. It is a great opportunity for organizations to retool routine business and technical processes using AI technology. It is also a great consideration for the software consulting services company engaged in developing custom applications. AI will lead the business with greater efficiency, better accuracy, and improving the bottom-line as well.
2. Low-Code and No-code tools in frontline
After this pandemic, global business has observed five years of digital transformation within five months. Low-code and no-code platforms come to the front line of future software development. Low-code and no-code tools are now shining by building custom business processes and apps for businesses with minimal IT support in the blink of an eye.
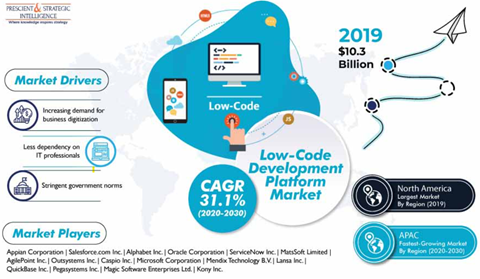
Software consulting firms are now more adhere to this platform as it allows citizen developers with minimal knowledge of hand-coding and makes the delivery faster with pre-packaged templates, graphic design, and drag-n-drop options.
3. Switch to machine learning operation
Machine learning operations are now highly recommended for an advanced modicum of operational excellence. In MLOps, the automated concept drift-detection allows us to check how production data differ from the data used to train the model. Based on the real-time feedback on the KPI model of production software services companies provide pre-build support to their clients and successfully update the model in the production phase with the support of AutoML integration. Software consulting companies are also applying the same machine learning techniques for successful software application development.

4. Automated evaluation of code quality
Code quality is the first consideration of every software consulting firm in building any software because without readable, scalable, and maintainable code they cannot run the application successfully. Considering it, experienced engineers pay more attention to developers’ coding capability at the time of hiring. In the voice of Tigran Sloyan, Code signal, the manual code review is a lengthy process, but with advanced AI and machine-learning techniques, it will be automated very soon.
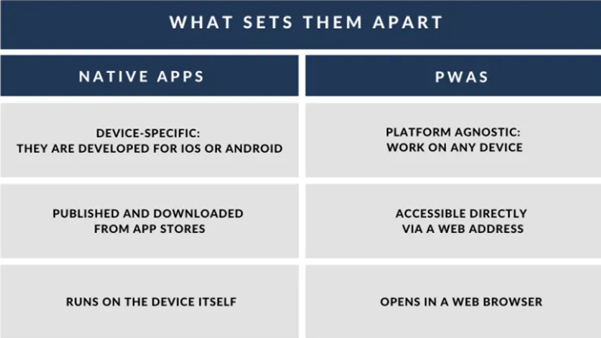
5. Progressive custom web app
Progressive Web Applications are the latest generation of mobile-optimized websites. According to Gartner’s research, Progressive Web Apps will replace 50% of all customers facing native apps by 2020. Software consulting companies are now giving more preference to these PWA as it shares many of the same functionalities as native apps and provides an identical user experience.
6. Python squeezes its competition
According to software services companies, Python’s robust growth is likely to be continued in 2020 and beyond. We all know that computer languages are always growing to shift and evolving but, Python has magically edged out Java for the top spot.
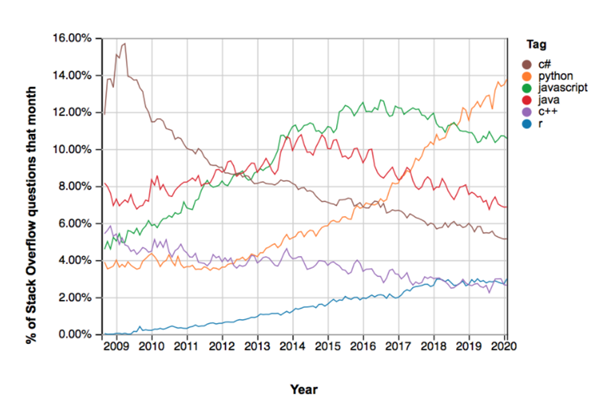
As per the opinions of the corporate leaders, Python is an easy-to-learn language, and spontaneous syntax makes it a transcendent language for beginners. Open source and versatile features make Python an ideal choice for start-ups and mid based software consulting firms. With so much popularity this trending programming language of 2020 reached Version 3.8.1 from version 1.0.
7. User-experience design
According to the Forrester Research report 2019, on average, every dollar invested in UX brings $100 in return with an ROI of 9900%. For every business. In that context, User Experience designs have entirely shaken the ground of how custom applications were developed to address user challenges, and now it is time to explore how the UX principle could play a pioneering role in defining a product or service roadmap. In the view of IT consultants, user experience led software design is critical for redesigning customer-facing services and allow companies to recapture their business in the present all-digital environment.
8. Motion UI
In 2020 and beyond, we will start seeing a less static website with more applications of motion UI. It is the most user-centric and sophisticated approach for a design that makes the website more expressive and even user-friendly. For example, a user clicks on a button will redirect them to a page with new information along with the moving effects on the screen. According to Thomas Griffin, Motion UI can connect dots and improve user journeys that a static image or a screen cannot.
9. Edge computing and FAAS
For a long time, the cloud-based IaaS and PaaS technologies have helped many organizations to accelerate their delivery while the majority still require a nonredundant service for isolated geolocation. The shift to FaaS (functions-as-a-service) is the next big evolution that will host at the very edge of our cloud and CDN networks.
10. The integration of DevSecOps
Within modern software development, shifting security and integrating DevSecops combine with automation is the next big future trend. Developers can not overlook the security nor allowed waiting until the later stages of the software development life cycle to ‘take on’ security. Software services companies apply threat modeling automation as it enables them to detect, prioritize, and mitigate threats from virus attacks in the design phase.
11. Perfection with digital experience
A perfect digital experience went from a novelty to a table stake in a blink of an eye. Front-end development takes center stage as the number of applications skyrockets, and cloud infrastructure becomes ubiquitous for software development services. As per McKinsey build up the next-generation operation model is the most crucial part of digital experience in development. It allows business free from all constraints (decision-making bureaucracy, tech infrastructure, business-historic culture) innovative talent that can push the envelope and hatch new business models—your in-house Internet start-up.
In short, we can say that modern software development is all about building solutions that take advantage of technology offer using the different architectures, services, and capabilities available to maximize the benefits. It also increases interpersonal skills and improves the collaborative approach to maintain harmony with the context of use and customers.
Now organizations are paying much attention to fundamental concerns like security, privacy, and ethical responsibility with modern software development practice. We hope in the future Modern software practice will make developers more eligible with better techniques and technologies. If you also want to apply modern software development techniques for your business, then feel free to reach us. We are here to help you!